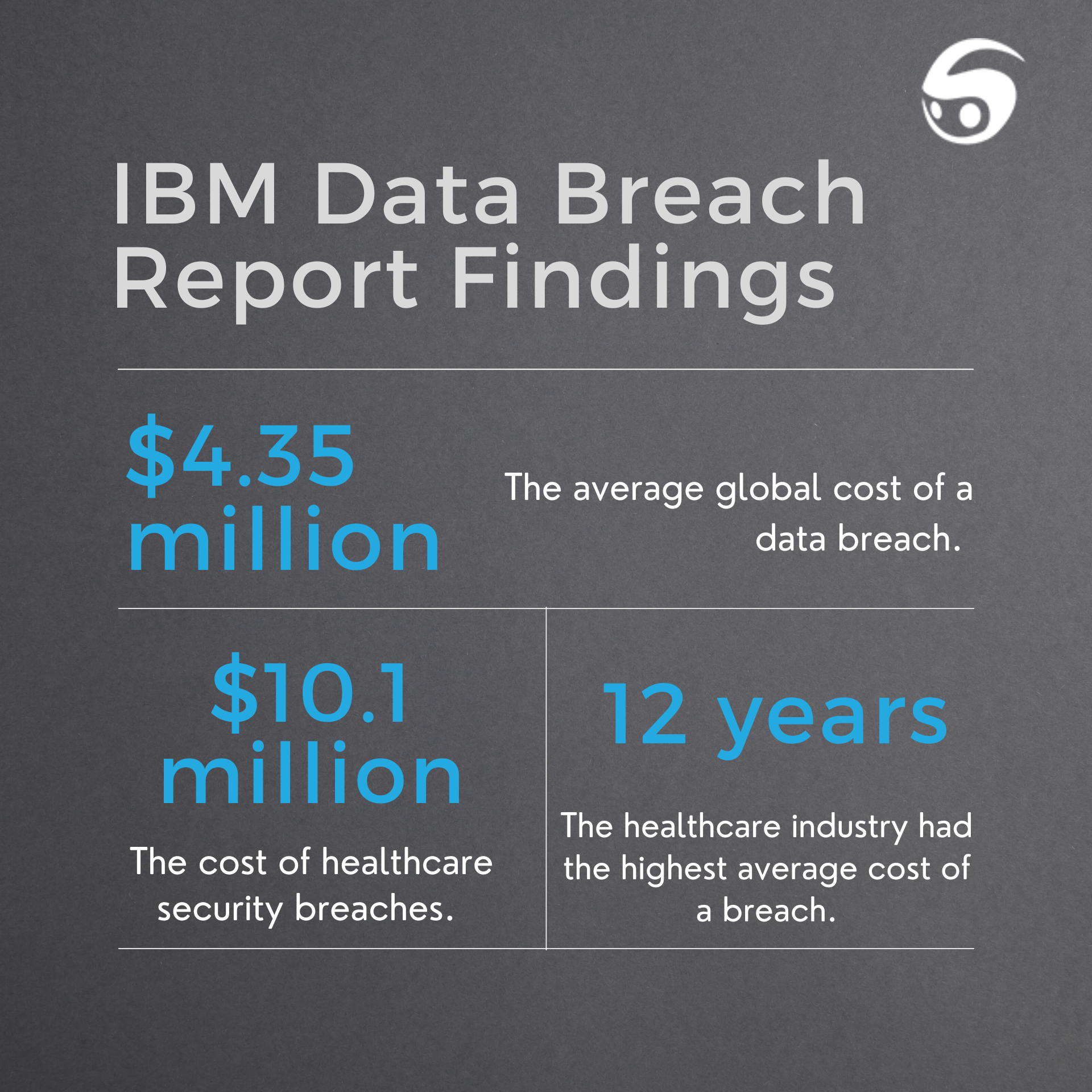
Security breaches and cybersecurity attacks have devastating effects on organizations. The latest IBM’s Cost of a Data Breach 2022 Report identified that the average global cost of data breaches reached $4.35 million in 2022 alone – a 2.6% increase from 2021.
Healthcare security breaches run deeper in cost, totaling to $10.1 million for 2022 – a record high for healthcare. In fact, IBM’s report detailed that healthcare breach costs have been the most costly of all industries for 12 consecutive years. Furthermore, these costs were found to accrue in later years following the initial breach, resulting in long-tail costs.
Fortunately for organizations using Software as a Service (SaaS) technology, such as vendor management systems or other service programs to manage operations, there are a variety of standards to ensure security measures. One such assurance is a System and Organization Controls 2 (SOC 2) audit and report.
A SOC 2 audit and accreditation is the golden standard for SaaS providers or service organizations to demonstrate their commitment to information security of their clients. A SOC 2 refers to both a set of criteria and an evaluation of a third-party organization’s controls. An organization is thoroughly evaluated on SOC 2 criteria to determine legitimate security practices of their system controls that ensure data security.
This blog aims to clarify what a SOC 2 report is and why it’s critical when managing healthcare operations through external service providers.
What is a SOC 2 Report?
A SOC 2 is both a security framework and audit established by the American Institute of Certified Public Accountants (AICPA) to ensure third-party organizations are managing customer data and system controls effectively and securely.
The security framework of SOC 2 is based on an organization’s compliance around 5 key categories. The Trust Services Criteria (TSC) are the 5 categories that third-party organizations need to be compliant with to successfully earn a SOC 2 report.
The 5 Trust Service Criteria are:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
Audits are performed by independent Certified Public Accountants (CPA) that evaluate an organization’s controls based on SOC 2 requirements and compliance to the 5 categories. If successfully compliant, an organization will receive a SOC 2 report that can be shown to clients to confirm safe security measures.

SOC 2 Report Types
There are two SOC 2 Report types an organization can receive. Organizations can opt to qualify for one report or both.
SOC 2 Type 1 Report: controls and systems are compliant at a specific point of time.
SOC 2 Type 2 Report: controls and processes are compliant over a period of time (usually 6 to 12 months).
Why a SOC 2 Report Matters
Using services or software that are SOC 2 certified signals that organization’s commitment to security through ethical and solid security practices. A SOC 2 report is a competitive advantage for service organizations to establish credibility and trust among their clients.
Healthcare organizations routinely use several forms of technology and third-party services to successfully run daily operations. Greater reliance on technology means healthcare facilities need to ensure high levels of safety measures from the beginning to prevent cyberattacks. Failure to invest in proper safety measures or partnering with third-party organizations that neglect to follow best practices can result in devastating costs for health systems.
A Secure VMS
Ensuring security best practices to prevent cyber breaches and protect client data is a top priority for StaffBot. StaffBot’s healthcare-tailored VMS is SOC 2 certified for both Type 1 and Type 2 reports to ensure protection within your healthcare facility. Test drive our user-friendly system and determine if a VMS is the right solution to your contingent workforce objectives. Schedule a demo below!
Connect with an expert or request a demo
"*" indicates required fields





0 Comments